October 25, 2019 - Comments Off on What is Ransomware And How can you protect Yourself
What is Ransomware And How can you protect Yourself
The DRF’s helpline has noticed a marked increase in complaints regarding ransomware attacks in Pakistan. This increase means that such attacks are becoming more commonplace, and it would be good practice to protect our devices and software against such malicious software.
Ransomware is a term most people talking about these days. It is a malicious software that enters your hard drive and encrypts all your files, rendering them inaccessible, until you get the decryption key. It increases its area to the level where cybercriminals targeted big giants but also hunted civilians and average users as well. On different social sites, a lot of people talked about the message that appeared on their devices while opening up their document, which asked them to pay a ransom in bitcoin or through another medium to get their files back in a readable format.
There are different Ransomware that belonged to separate families, which has further different variants. You need to check which family ransomware belonged to and what is the variant if you faced a ransomware attack. You can check it by looking into the extension of the encrypted file like in “picture.png” where “png” is the file extension.
Some examples of the Ransomware Attacks:
You all are well-aware of the ‘Wannacry Ransomware’ Attack of 2017. This attack was massive and infected entire devices and databases. It affected many businesses, hospitals, and other big networks across the globe. The malware didn’t leave behind banks, and mobile operators either. It affected companies in over 100 countries.
Petya ransomware was also in the news after wanna cry Ransomware, which is specifically targeted a windows-based operating system and encrypt the whole hard drive, and to make the files accessible, you need to pay some money in bitcoin.
Following these two major attacks, the FBI sent out a public-service warning about such malware. According to them, these software are getting more advanced and can penetrate larger and ‘more secure’ systems.
Pakistan has also been affected by ransomware as well. Different variants of ransomware software were found to be affecting Pakistani businesses and individuals. Over the past few months, the DRF helpline has seen a large number of calls come in regarding ransomware and a lot of them had to do with a ransomware strand called ‘Stop’.
How it Works:
Ransomware is a type of malware that anonymously injects into the digital devices that encrypts all the content stored on your hard drive, and you cannot read your files anymore. To get your files in a readable format, a decryption key is required, which will then unlock all the files. However to get that decryption key, you must pay a ransom.
This creates a bit of a dilemma. Are you going to pay money to get your files back, or are you encouraging cyber criminals so they can spread this malware to target more people?
Paying ransom itself is a bad practice because there is no guarantee that you will get your files back, and in any case. Let’s suppose if you pay money to the attacker that they asked for, there are still chances that the attacker will not have a private key, or the key they gave to you is corrupted. So paying money to the attacker is not good practice as there is no guarantee that he will unlock your content. Let’s say you successfully managed to get your data back, on the other hand, the attackers start hunting more people.
This is only the first step you have to take if you faced a ransomware attack.
The second step is that you need to disconnect the internet from your devices so it cannot do further damage to your device and don’t spread the malware within the network. After this, you have to run an anti-malware tool in your device, and if it finds anything, remove it and restart your computer. If you don’t do this step and unlock your file, the malware is still in your system, which will reactivate itself. Additionally, whenever you see a ransom note appear on your device, it would be good practice to take a screenshot and send it to experts who can help you decrypt your files.
Sometimes while running an anti-malware software, corrupted files can be deleted in order to protect your device. This leads to a permanent loss of data. To avoid this from happening, the user can create a backup of the files on an empty external hard disk in order to prevent loss of data before running the anti-malware software. Once a decryption toolkit is made for the particular ransomware that affected your device, these files can be decrypted and restored.
There are many ways an attacker can infiltrate the network or can compromise your device. Cybercriminals can exploit your device, and usually, they take advantage of outdated versions of operating systems or software installed on your device.
Avoiding Ransomware Attacks:
- If you received any suspicious attachment within the email, do not open it until you verify the source of this email
- Make sure you are using an updated version of the operating system or software installed your device
- Do not install unverified software into your device
- If you received any suspicious short link via WhatsApp or Facebook or any other platform, copy the link and open the website link and paste the link there. It will show the actual website link behind the short link. This is just good practice to identify if someone wants to trick you.
- Do not let someone attached USB into the USB port of your device.
- And the most important thing is to make a local backup of your data
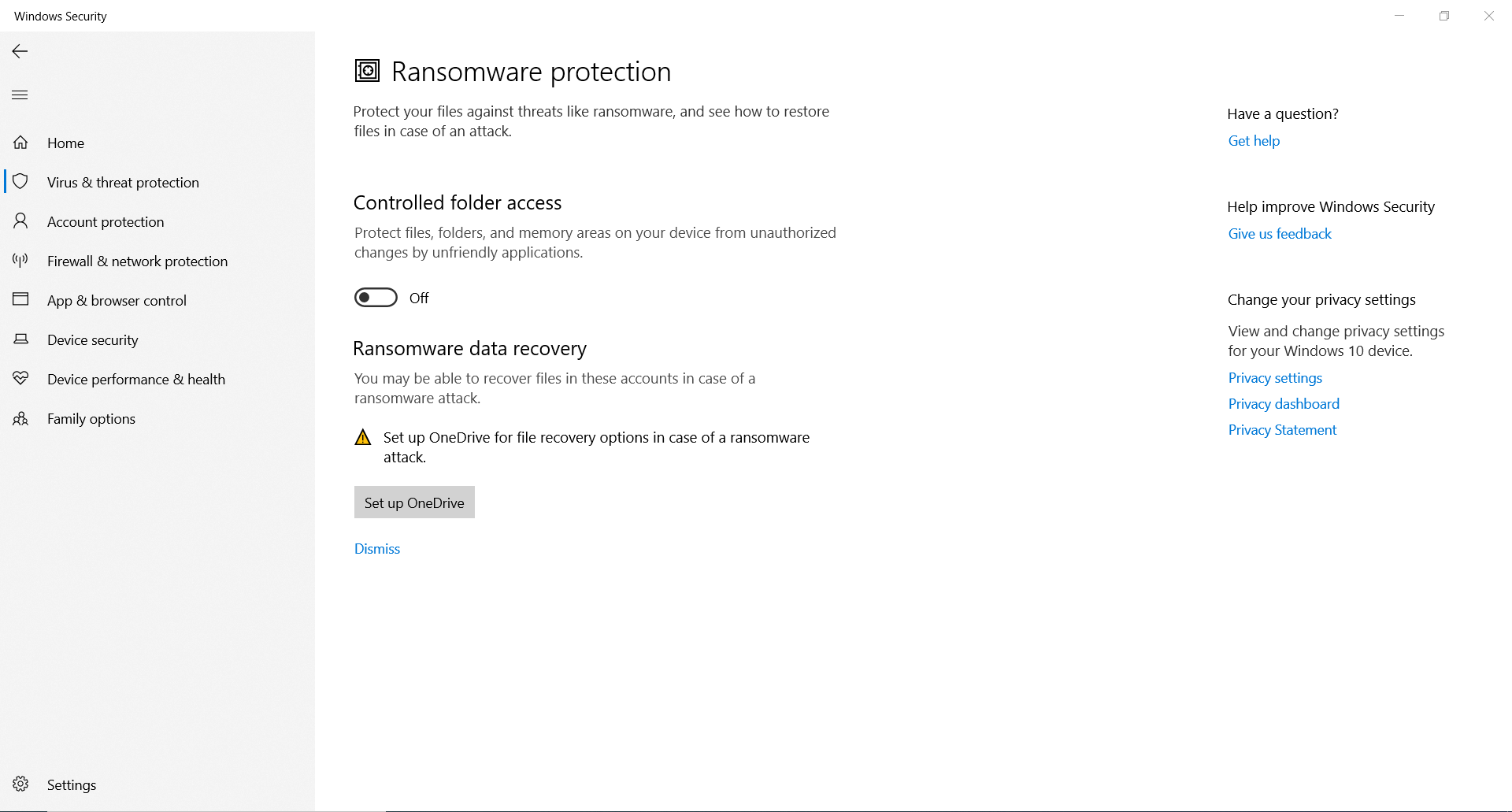
Microsoft’s built-in ransomware protection:
Microsoft recently introduced the feature known as ransomware protection, which users can use to protect the folder they want. You can enable this feature by going into the ransomware protection section.
You can find the whole sequence below:
Setting---> windows security--->virus threat protection--->in ransomware protection section click on---> Manage ransomware protection
Below is the screenshot
You can turn the above option “controlled folder access” on and pop up will appear, which asks your permission, and then you can see the list of protected folder and can add any folder you want.
In the above picture, you can see the protected folder. This means that no third party unverified software can make changes in the folders mentioned above, thus lowering the risk of data being compromised. If any unverified application tries to make changes in the folder that is already listed in the above directory, an error will appear at the user’s end.
(Note: In order to use Window’s anti-ransomware features, you must have the most up to date versions of Windows 10.)
nomoreransom.org is the project where different IT security companies and law enforcement agencies are trying to help the people who got ransomware attacks on their devices and don’t know how to proceed further. They update their website regularly with new information on ‘trending’ ransomware attacks and software. With this, they release a decryption toolkit that can be used by victims in case of an attack. File uploading option is also available for the victim to check if there is decryption toolkit available for that specific variant. A feature on this website allows for users to upload the affected files. This feature, called the ‘Crypto Sheriff’ determines whether there is a solution. If there is, the ‘Crypto Sheriff’ will provide the victim with the solutions needed. You can access ‘Crypto Sheriff’ here
Map of US ransomware attacks from 2018 to present
Aside from Window’s internal ransomware protection, there are multiple anti-malware tools one can use to protect their devices. One such tool is ‘MalwareBytes’. This software is able to conduct comprehensive scans and can identify threat. Additionally the software will quarantine and delete the affected files.
The DRF Helpline was established to help victims of online harassment. This includes people who have fallen victim to sensitive data leaks, and in recent times, ransomware attacks too.
The helpline can be reached at its toll free number, 0800-39393
Published by: Digital Rights Foundation in Blog


Comments are closed.