May 10, 2016 - Comments Off on Pakistan: A top malware destination?
Pakistan: A top malware destination?
Microsoft released its annual Security Intelligence report in the first week of May, covering the last half of 2015, from June to December. This report, now in its 20th volume, examines and breaks down what the Seattle-based tech company calls the “threat landscape of exploits, vulnerabilities, and malware using data from internet services and over 600 million computers worldwide”. According to the company, Microsoft looks as upwards of at least “10 million attacks” a day – nearly half of which originate in Asia.
To gauge which countries are the biggest targets for malware, Microsoft gathers the data from global computer systems that run its security software in real-time, reporting all incidents of malware attacks, regardless of success penetration or not – this metric is referred to Microsoft as the "encounter rate". Another metric used is the "Computers Cleaned per mile" or CCM, which is defined as the number of “computers cleaned for every 1,000 unique computers executing the Malicious Removal Tool (MRST)”, a free tool Microsoft uses to clean or remove over “200 highly prevalent or serious threats from computers.
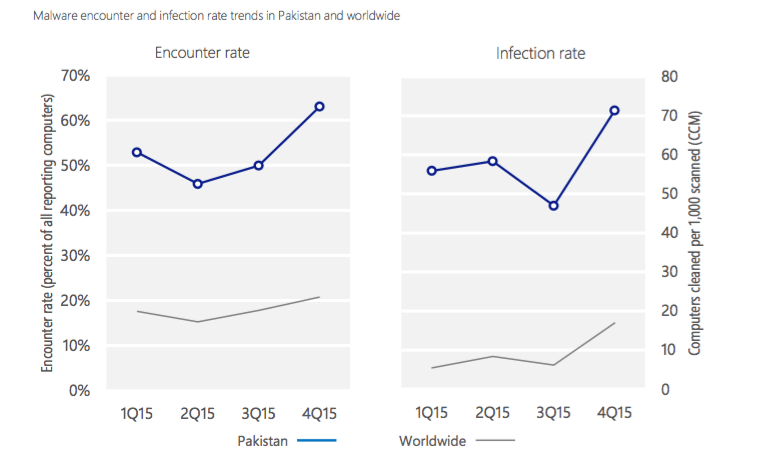
Infection & CCM Graphs, indicating malware attacks in 4Q2015, regardless of success or otherwise. Courtesy of Microsoft.
Utilising the "encounter rate" and CCM metrics, what Microsoft found was that the countries that were most under threat from attempted malware attacks last year were Bangladesh, Palestine, Nepal, Indonesia, and Pakistan. They found that while the worldwide encounter rate and CCM by the end of the last quarter of 2015 were 20.8% and 16.9% respectively, Pakistan experienced a 63% encounter rate, and a CCM rate of 71.3%. The three most common forms of malware attacks that Pakistani computer systems were experiencing by the end of the last quarter of 2015 were:
- Worms, “encountered by 35% of all computers”, marking an increase from 25.6 in the third quarter of 2015;
- Trojans “encountered by 25% of all computers”, marking an increase from 23.3 in the third quarter of 2015;
- Viruses “encountered by 11.6% of all computers”, marking an increase from 8.5 in the third quarter of 2015.
The Microsoft Security Intelligence (MSI) report on Pakistan, which breaks down what these numbers mean for users, can be downloaded here.
PLATINUM Threat
In addition to malware, the MSI report also covers the history and activities of a targeted activity group (TAG) that it has codenamed PLATINUM – a group that has garnered concerned interest due to its “aggressive, persistent tactics and techniques as well as its repeated use of new zero-day exploits to attack its targets.”
TAGs are generally opportunistic, with no fixed geographic target profile or attack strategy per se, looking globally. Much like other TAGs, PLATINUM shares an interest in stealing very sensitive intellectual property “related to government interests”. Where PLATINUM differs, however, is that unlike many other groups, it appears to have a specific geographic focus, in this case South and South-East Asia. Making use of “zero-day exploits” (where an attacker makes use of vulnerabilities in a computer system to exploit the system and networks) and “spear phishing” (target-specific phishing attacks), PLATINUM has targeted “governmental organizations, defense institutes, intelligence agencies, diplomatic institutions, and telecommunication providers.”
According to the MSI, PLATINUM has been able to carry out several “espionage campaigns” going back to 2009, making use of custom software tools and techniques to access their desired data, and then in turn make efforts to delete any trace of their “infection tracks.” The length and breadth of their activities, not to mention their focus on state data, could indicate either funding and support from a state actor, or a private group funding for the same reason. More information can be found on PLATINUM, and its troubling implications for national security mechanism in South Asia and South-East Asia, can be found here.
Keeping the entire blog in account, the best practice for everyday internet user would be stay safe in every way possible. Basic human practices such as changing passwords frequently and not clicking unknown links would benefit in a larger scale
There are concerns that we have with this report by Microsoft, however, which users should note: the report does not make mention of malware attempts on other major operating systems such as Apple's OSX, or Linux. The lack of mentions of Linux is especially important, as a growing number of governments are looking to move away from proprietary OSes such as Windows, and towards open source alternatives – usually modification of Linux distributions - that can be tailored to be more stringent and with less bloat present.
Microsoft itself has come under fire in recent years, due to its heavy retention of, and demand for user data – which this report is itself is heavily reliant on – present in Windows 10, gathered via data collection from a number of input devices and services, such as: location, camera, microphone, speech, inking, typing, account info, contacts, calendar, messaging, radios, devices, feedback, diagnostics, and background apps. These demands, as well as the keylogger built into Windows 10, put the private data and security of users at risk, and conversely make systems running on Microsoft products much more appealing to malware operators.
The findings of the report, however, do have merit: to be as safe as possible, it is important that all internet users implement best practices to safeguard their security, especially at a time when malicious attacks are evolving. Simple techniques such as changing passwords frequently, not clicking on unknown and suspicious links, and keeping systems up to date are just some of the small steps that users can take to defend themselves.
Written by Adnan Chaudhri
Published by: Digital Rights Foundation in Blog

Comments are closed.