August 22, 2014 - Comments Off on Pakistan is a FinFisher customer, leak confirms
Pakistan is a FinFisher customer, leak confirms
In the first week of this month, someone hacked into the servers of FinFisher, the notorious surveillance software maker, which was reported to have two command and control servers inside Pakistan last year. The hackers got hold of whatever they could find on the server and leaked it as a torrent. The 40Gb torrent contains the entire FinFisher support portal including the correspondence between customers and the company staff. It also contains all the software that the company sells as well as the accompanying documentation and release material.
What is FinFisher?
FinFisher is a company that sells a host of surveillance and monitoring software to government departments. The primary software, FinSpy, is used to remotely access and control the computers or mobile phones belonging to the people being spied on. The company offers several methods to install FinSpy, which range from a simple USB that can infect a computer to directly attaching the trojan with legitimate files when they are being downloaded through installing a kit at the ISP. The whole FinFisher toolset is designed to give the people buying these software access to emails, web browsing history, and any other activity performed by the “targets".?
Is Pakistan a FinFisher customer?
Apparently, yes. A University of Toronto based research group called Citizen Lab released a report last year identifying two FinFisher command and control servers on the PTCL network. But this recent leak gives us a more complete and conclusive picture. The leaked support portal tells us that someone from Pakistan in fact licensed three software from FinFisher for a period of three years. The systems Citizen Lab identified were probably the computers hosting the FinSpy server program and were merely using a PTCL DSL connection. PTCL, the company, we think was not involved. If not PTCL, then who? It could be anyone but since FinFisher only sells these software to government agencies, it was most likely one of the many intelligence agencies operating within the Pakistani government.
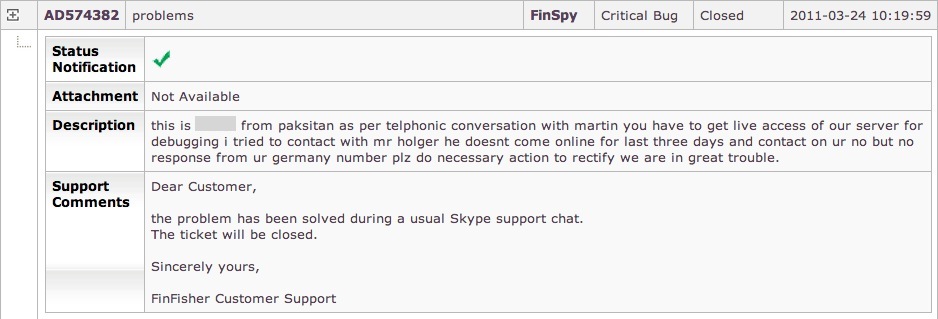
In one of the “critical"? support ticket that we have extracted from the FinFisher support portal, someone identifies their name (retracted in this article) and location (Pakistan) and complains that their problems are not being addressed through Skype (which we presume was the primary way FinFisher provided help to the customers). FinFisher database identifies the said customer with the username 0DF6972B and ID 32.
What was purchased?
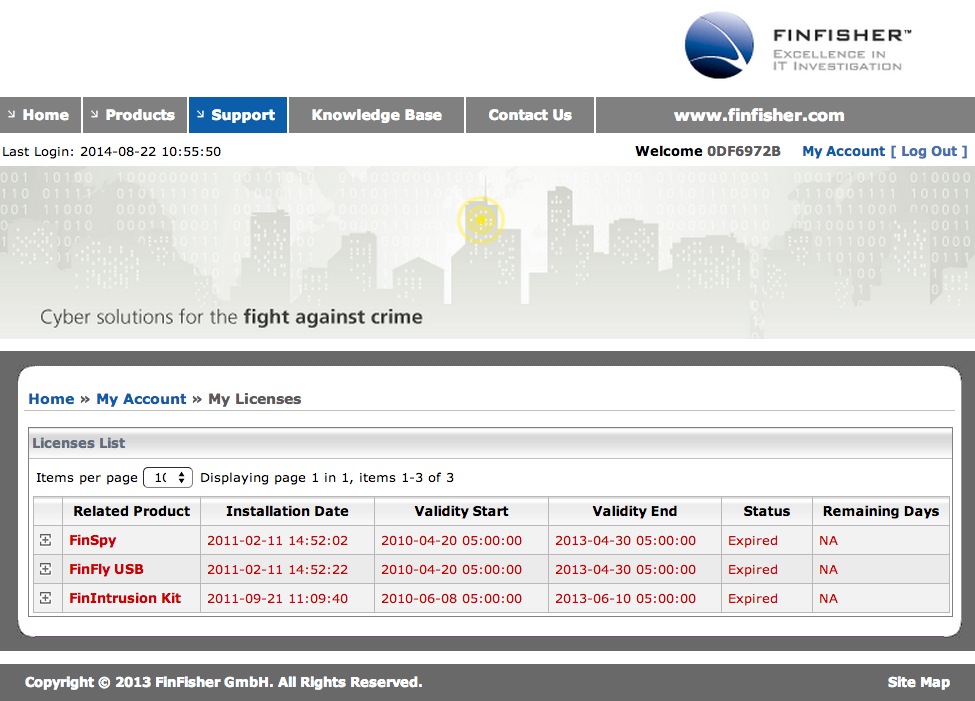
After that clue, we looked further into the purchase history of Customer 32 and their correspondence with FinFisher staff and found out that they have licensed not one but three software from the spy software maker. The primary software, FinSpy, is used to target people who “change location, use encrypted and anonymous communication channels and reside in foreign countries.�? After FinSpy is installed on a computer or a mobile phone, it can be—according to the product brochure—“remotely controlled and accessed as soon as it is connected to the internet/network.�?
In addition to FinSpy, Customer 32 also purchased another software called FinIntrusionKit to hack into hotel, airport, and other wifi networks to catch “close-by WLAN devices and records traffic and passwords�?, extract “user names and passwords (even for TLS/SSL encrypted sessions),�? and “captures SSL encrypted data like webmail, video portals, online banking and more.�? The third software is a tool to infect USB devices so that whoever plugs them becomes a target of surveillance.
How does Pakistan FinFish?
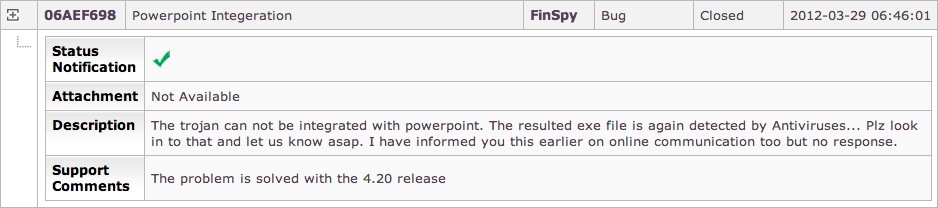
From the support tickets filed by Customer 32, we also get to know that whoever in Pakistan purchased FinFisher used it, for instance, to infect harmless MS office documents, particularly PowerPoint files and sent them to people they wanted to spy on. The simple act of opening the infected files led their computer being put into constant surveillance including emails, chats, and other activity.
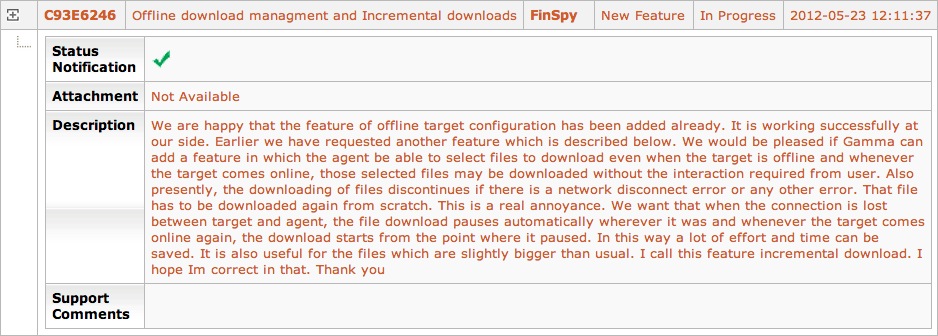
Customer 32 also used FinFisher to covertly steal files from the “target�? computers. All the files of those who were targeted were readily available but Customer 32 wanted more, as outlined in another support ticket: “the agent be able to select files to download even when the target is offline and whenever the target comes online, those selected files may be downloaded without the interaction required from user.�?
While we know that FinFisher is deployed in Pakistan, some questions remain to be answered. As citizens of a democratic state, it is our right to know who is using these surveillance software in Pakistan, how much budget is being spent on these licenses, and what laws and regulations are being followed for deploying these software.
Update [Sep 15, 2014]: How much did it cost?
WikiLeaks today released a list of countries who bought software from FinFisher and the associated cost that was paid. The cost was calculated using a price list they found inside an excel file. Pakistan, as per the revealed price list, paid €432120 (or 57 million Pakistani rupees) for the three software that were purchased.
Published by: Digital Rights Foundation in Blog

Comments are closed.