November 10, 2014 - Comments Off on Inside FinFisher: examining the intrusive toolset
Inside FinFisher: examining the intrusive toolset
FinFisher, a company known for making and selling a wide range of spy software to world governments for large sums of money, was hacked in the first week of August this year. The anonymous hackers leaked a 40GB torrent including the entire FinFisher support portal with obfuscated information about the buyers, list of software they had purchased, duration of each license, and their communication with the support staff. The leak helped human rights activists around the world identify the buyers, hold their governments to account for the purchases, and question the necessity of such a measure. Digital Rights Foundation also released a report detailing the evidence of Pakistan’s purchase of three software from FinFisher.
The leak generated a lot of buzz and rightly so. But the coverage from mainstream media and human rights organizations was primarily limited to reporting the leak, identifying the buyers, and potential human rights implications. There hasn’t been an in-depth coverage of the scope and capabilities of the whole set of software FinFisher sells. This is what we intend to do in the current article.
Understanding FinFisher
FinFisher is not just a software. It’s a well-thought-out and sophisticated toolset, comprising of both software and hardware, built from the ground up to gain access to people's private data and communications. Well thought out in the sense that each tool compliments the others in breaking into someone’s communication and sophisticated in the way the tools are generally invisible to the person.
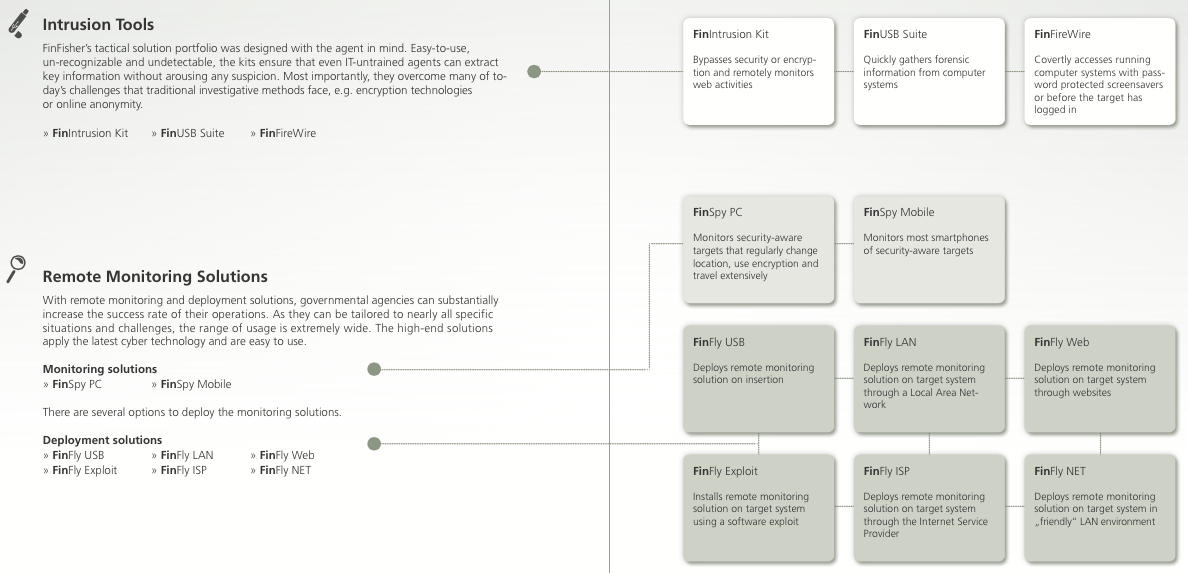
An overview of the FinFisher toolset; please click on the image to enlarge.
At the time of the leak, FinFisher had 12 products available on its website: ten hardware+software solutions to break into computers and mobiles, a repository of 0-day and 1-day exploits that can be used to infect the target systems, and a training program. Among these solutions, FinSpy is the jewel of the crown. It is a remote monitoring solution that is capable to basically let the buyer see everything someone does on their computer.
How Do They Break In
It is easier if they, or anyone they know, have access to the computer. FinFisher offers three solutions for this situation. Two of them (FinUSB Suite and FinFly USB) involve attaching a USB drive to the computer, it does not matter if the computer is shut down or logged in, password protected or not. Once the USB is attached, the system becomes compromised. Third one (FinFireWire) is a set of adapter cards (FireWire/1394, PCMCIA and Express Card) and associated cables that, when attached, give access to a running but password protected Mac, Windows, or Linux computer.
Four FinFisher solutions are designed for the situations when they don’t have physical access to someone’s computer.
FinFly Net consists of a small portable computer that is attached to the router of a hotel or airport or any other “friendly” place and a laptop. Once the FinFly Net computer is The management laptop can then see internet traffic being sent and received by the people attached to the network. It can also display a fake software upgrade notification to the target, which when installed, gives complete access to that computer. Since this solution sits between all internet traffic going to and from the people connected to the network, this solution is also capable to insert a software update (Adobe Flash, for example) notification on a legitimate website.
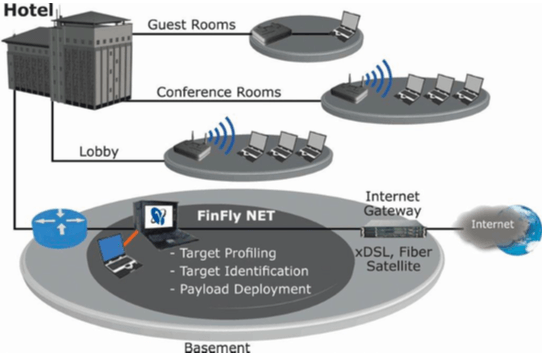
FinFly LAN can also attach spying software with legitimate files on-the-fly, while being in the same wired or wireless network. FinFly Web creates fake websites which make use of the loopholes in web browsers to instantly install FinSpy, the crown jewel in the FinFisher toolset.
FinFly ISP is a hardware solution deployed at an ISP to covertly install spy software to any computer in a city or country. This solution is able to “patch” any legitimate files being downloaded by people with a spying software. Like FinFlyNet, it can also issue fake upgrade notifications for popular software like iTunes. The computer becomes compromised as soon as the downloaded files are run or software upgrade is applied.
FinIntrusion Kit is an advanced toolkit that includes a customized Linux laptop with a host of adapters and antennas and can break WEP and WPA/WPA2 passphrases.
What Can They See
A lot. But let’s go through it step by step.
IN CASE OF PHYSICAL ACCESS
FinUSB toolkit can extracts login credentials from common programs like email clients, chat messengers, and remote desktop tools. It can also silently copy recently opened, created, or edited files from the computer as well as browsing history, chat logs, and wifi passwords.
FinFireWire, after bypassing the login or lock screen, can recover passwords from RAM and copy all files onto an external drive.
IN CASE OF CLOSE PROXIMITY LIKE AIRPORTS HOTELS
FinIntrusionKit, which only requires the target to be on the same network like airport or hotel, can capture usernames and passwords being entered on websites, in addition to any other internet traffic, even if it’s on HTTPS.
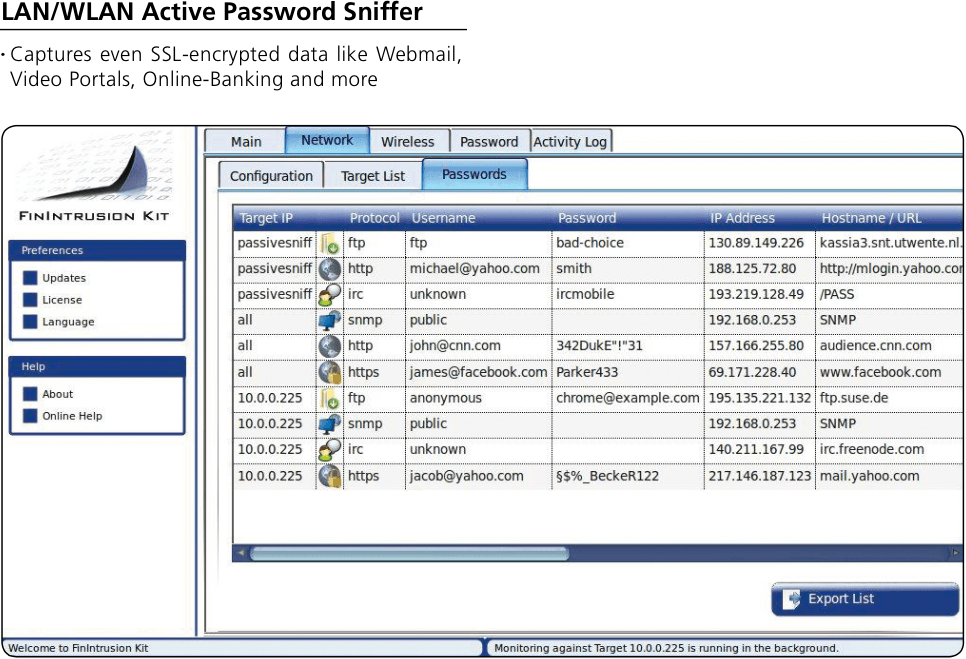
FinFly Net and FinFly LAN lead to the installation of FinSpy which then gives full access to all data and communications for a system.
IN CASE OF NO PHYSICAL ACCESS OR PROXIMITY
FinFisher provides FinFly ISP and FinFly Web to infect people who are not in close proximity. Once infected, full access to these computers will be granted.
A video detailing how FinFly ISP works
FinSpy: Jewel of the Crown
Marketed as a ‘remote monitoring solution,’ FinSpy is the multi-purpose spying software around which the whole company revolves. It gives opens a backdoor to the infected computer allowing for live access to all files and data. It also enables access to the mic and webcam installed on the computer for “live surveillance.” It can also save an audio or video recording of each Skype call and send it to the buyer. And it can, FinFisher flaunts, “bypass almost 40 regularly tested antivirus systems.”
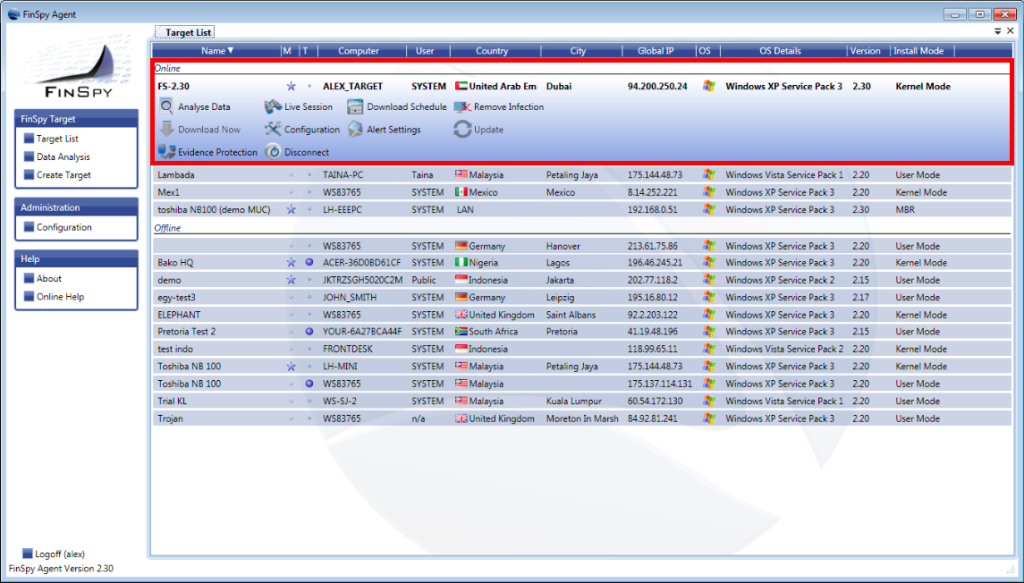
FinSpy Control Center. Click on the image to enlarge. Note the area in red: Those are the actions that can be taken on an infected computer.
We have a saying in Punjabi to seek refuge from something terrible: May this not happen even to my enemy. I'll end this post at that.


