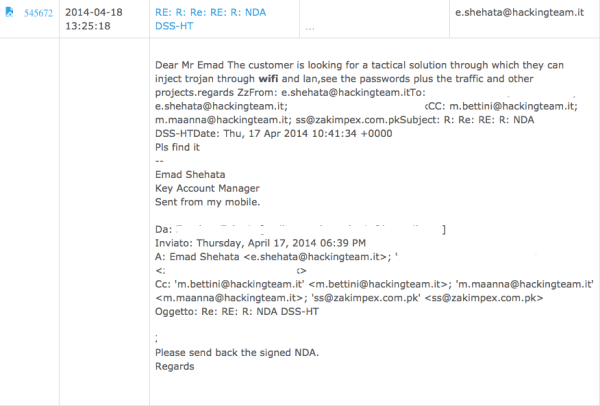
July 24, 2015 - Comments Off on Unlawful Interception: Pakistan’s intelligence agencies, Hacking Team, & the abuse of communication surveillance powers
Unlawful Interception: Pakistan’s intelligence agencies, Hacking Team, & the abuse of communication surveillance powers
Earlier this week, Privacy International released their in-depth report on the state of surveillance in Pakistan, Tipping the scales: Security & surveillance in Pakistan. Available to the public, the report examines the exponential rate at which communication surveillance measures have been undertaken by the government of Pakistan defended as being necessary to combat internal and external threats to the nation. However, while it is the role of the state to protect its citizens from internal and external threats to their life and liberty, this echoes an all too common rationale used by foreign governments and intelligence agencies worldwide to justify ever increasing surveillance of their own citizens, and to limit or remove the legal rights of those same citizens to push back against the invasion of their privacy.
The “Global War on Terror” has seen law enforcement agencies worldwide request and in most instance receive millions in “anti-terrorism” funding, as well as broader powers with oft-generous leeways, to tackle terrorism as they see fit. Armed forces, intelligence agencies and law enforcement departments worldwide will direct such largesse towards the acquisition of and greater access to technologies that allow them to spy on their own citizens. Since September 11 2001, this had led to the rights of citizens abroad violated by their own governments, who will carry out surveillance without proper public oversight – if at all. Activists, journalists, politicians and other ordinary citizens with no link to terrorist groups whatsoever have found themselves under observation, and often without any legal recourse.
As a partner in this “War on Terror”, Pakistan is no different, with its military forces receiving generous levels of funding from the government as well as from its international allies, to tackle its own conflicts against armed militants. It has also given broad powers and authority to state agencies, to tackle what they argue is language and behaviour that is detrimental to the reputation and safety of Pakistan. Coupled with bans on encryption and forms of proxy software, what this has led to, according to Privacy International's report, has been an abuse of:
"...their (Pakistan's intelligence agencies) communication surveillance powers, including spying on opposition politicians and Supreme Court judges. Widespread internet monitoring and censorship has also been used to target journalists, lawyers and activists."
Privacy International's report also reveals that Pakistan's Inter-Service Intelligence Agency (ISI) wanted to expand their surveillance capabilities via the commission in 2013 of a:
"mass surveillance system to tap international under- sea cables at three cable landing sites in southern Pakistan. The “Targeted IP Monitoring System and COE [Common Operations Environments]” would allow Pakistan to collect and analyse a significant portion of communications travelling within and through the country at a centralized command centre. With a projected intake of an estimated 660 gigabytes per second, the system would amount to a significant expansion of Pakistan’s communications intelligence gathering capacities."
To create such a system to strengthen one's surveillance efforts, it has become de rigueur to reach out to the private sector for hardware and software surveillance solutions. A multi-billion dollar industry, commercial surveillance firms have found no shortage of potential clients in the wake of post-September 11th attacks attributed to terrorist organisations or lone wolves. The Privacy International report highlights how Pakistan's intelligence agencies and security forces, represented by partners in the Pakistani private sector, sought to purchase products and services to allow them to expand their surveillance abilities, to infiltrate the digital devices and computers of citizens, from international spyware firms.
Earlier this month one of these companies, the controversial Italian spyware manufacturer Hacking Team, was hacked. The firm's official twitter account was taken over on July 5, and links to over 400 GB worth of internal Hacking Team data were provided, which in turn were shared by WikiLeaks and others. This hack allows us to explore how Pakistani intelligence agencies purchase the technology and services they require for greater surveillance creep.
A controversial player in the commercial digital surveillance industry, Hacking Team has frequently asserted that it goes to great lengths to ensure that its software is not utilised to undermine human rights. The internal communications and invoices unearthed, however, strongly contradict the firm's claims. Communications with representatives indicate little concern made regarding misuse of HT's software packages to undermine human rights activities – they are, instead, reassured and informed that there will be no trouble in operating in particular regions. Hacking Team's core business centred around their Remote Control System (RCS) software suite, which allows customers to infiltrate the computer and mobile devices of targeted individuals and install backdoors, in turn allowing for undetectable monitoring at will. Hacking Team's RCS, also known as Galileo, allows customers to (according to their promotional material):
“Keep an eye on all your targets and manage them remotely, all from a single screen. Be alerted in incoming relevant data and have meaningful events automatically highlighted.
Remote Control System: the hacking suite for governmental interception.
Right at your fingertips.”
If the modus operandi of Hacking Team and Galileo sounds familiar, it should: Finfisher, a surveillance software package released by Gamma International Ltd in 2007, was brought to the world's attention in August of last year, due to a 40 GB leak that exposed the company's internal communications and financial history, as well as the governments that purchased – or were interested in purchasing – Finfisher for domestic surveillance purposes. Finfisher, like Hacking Team's RCS/Galileo software suite, allowed customers to infiltrate the computer systems of targeted individuals, and install software undetected. Digital Rights Foundation has covered Finfisher and how it operates here.
Finfisher's "Remote Monitoring and Deployment Solutions" and Hacking Team's RCS have something else in common: both were of interest to Pakistani companies, working on behalf of domestic military intelligence and intelligence agency clients. An examination of Hacking Team's leaked internal data uncovered email communications between Hacking Team and Pakistani IT company representatives between 2011 and 2015. Also uncovered were internal communications, mostly in Italian, between members of Hacking Team regarding their thoughts on potential Pakistani partners, as well as sharing and discussing news articles pertaining to the security situation in Pakistan and South Asia. Unlike Finfisher, the data leaked does not appear to indicate that a successful purchase of RCS/Galileo was made by Pakistani buyers.
"You can compare them to MI5": Pakistan's Interest in Hacking Team's Tech
The extensive data leak reveals the manner in which Hacking Team communicates with representatives of potential clients in Pakistan. Sensitivity is requested by representatives in regards to the identities of their clients; preferential treatment; verification of identities by clients, visa invitation letters; VIP guest ticket requests; interest in specific software and service demonstrations, and internal discussions regarding client representatives are covered in the emails. Below are samples of the email communications between Hacking Team and potential customers:
January 18th 2011 marks the earliest recorded communication (as collected by Wikileaks and other sources) between Hacking Team and Pakistani client representatives. Marco Bettini, HT's International Sales Manager, is in communication with Zeeshan Zakaria, Chief Executive of Defence Solutions & Systems Ltd (DSS), a Lahore, Pakistan-based company. The email, part of a long response thread entitled “R: R: R: R: Demokit” in response to Mr. Zakaria's previous email that states that there will be “4 guests who will see the demo. We will require you to do the demo.” In the email Mr. Zakaria also says that he will “appreciate if you dont (sic) offer your prices or product to anyone else in Pakistan for the time being.” Mr. Bettini asks for the name of the guest “in order to require the badges for ISS admittance” and if he, Mr. Zakaria, will be attending as well. Hacking Team does not”give any exclusivity based on country”, says Bettini, but they can “block” other companies asking for “any activity or quotation for the same customer” if Mr. Zakaria can provide the name of the agencies he is working with.
(As ISS comes up quite often in Hacking Team emails, it should be explained at this point that ISS in the context of the emails is an abbreviation of “Intelligence Support Systems for Lawful Interception, Electronic Surveillance and Cyber Intelligence Gathering”. The website for the ISS describes it as thus:
“ISS World Middle East is the world's largest gathering of Middle East Law Enforcement, Intelligence and Homeland Security Analysts as well as Telecom Operators responsible for Lawful Interception, Hi-Tech Electronic Investigations and Network Intelligence Gathering.”
In 2011, the ISS conference was held in Dubai from February 21-23, 2011. Among the conference's sponsors as of 2015? Hacking Team, Finfisher, and Gamma Group. Though a separate entity since October 1st 2013, Finfisher was established in 2007 as part of the Gamma Group.
The following day, an email from Ali Ahmed of Miran International – according to its website, a Karachi-based “company specialising in security, defence and telecommunications” - is forwarded by David Vincenzetti, Hacking Team's CEO, to [email protected], concerning an inquiry “from one the premier Intelligence Agencies in Pakistan” in regards to “infecting of GSM handsets.” (sic). Unaware of the earlier communication to HT by DSS, Miran International is interested in partnering with the Italian firm in Pakistan for the project if the latter has not already found a partner in the country.
"K Block" refers to the HQ of the Intelligence Bureau, at the Secretariat in Islamabad, Pakistan. Image Via Wikileaks.
The following day Hacking Team contacts Mr. Zakaria of DSS, asking him to provide the names of his guests. He is also informed by HT that they “are already involved in other opportunities in Pakistan.” “To protect your job,” the email from Mr. Bettini continues, “please inform me as soon as you can the agencies and contacts you are working with.” (sic). Following this email, Mr. Ahmed of MI is sent anemail by Mostapha Maana, Hacking Team's account manager for the Middle East region, similar to the one sent by Mr. Vincenzetti, asking for the agency letter, to check if they are already “in contact” with the client in question. It bounces back, and is sent again on the 21st by Mr. Maana. Mr. Maana gets in touch with Mr. Zakaria of DSS , and knows that “ we have been trying to work together since 2008”. As before, Mr. Zakaria is asked for the names of his clients “in order to protect your job”. Mr. Zakaria responds that “at this stage I think we should not discuss the names of the customers as it is a little sensitive.” Mr. Maana then responds, saying that he needs to know the names of the clients “otherwise I cannot refuse to meet the other Pakistan company at the ISS. By the way, I already know the name of this company's customer.”
It is at this point that Mr. Zakaria identifies the customer/client as being the National Police Bureau, with names of the officers attending the conference being named in the email. He requests that VIP invitations be arranged for the officers as “they are very interested your product.”
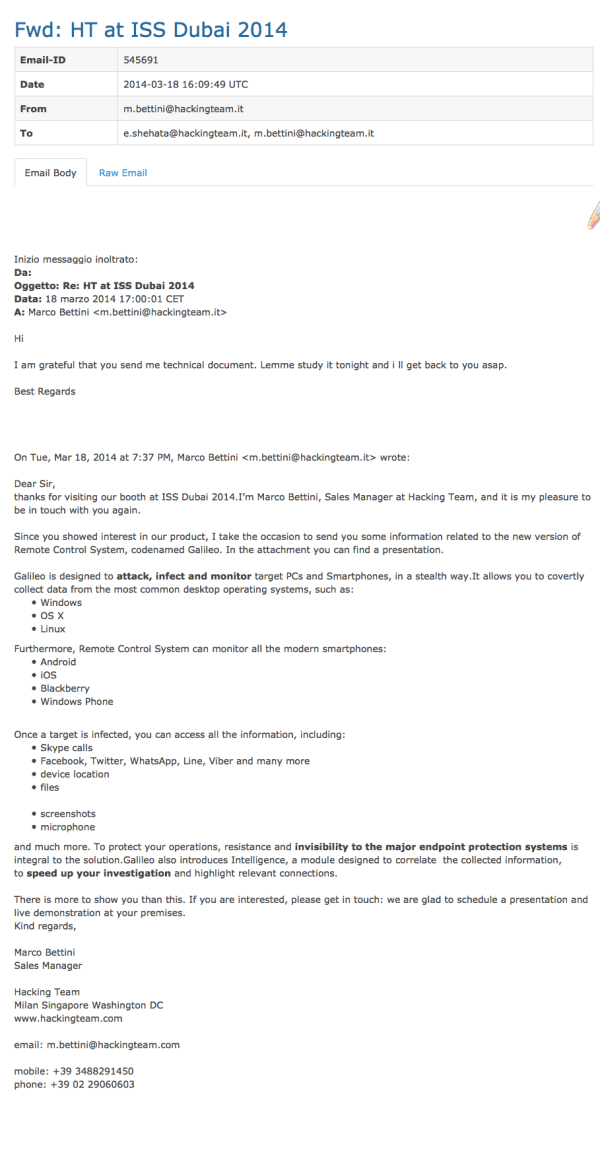
Hacking Team outlines to how RCS/Galileo works to the representative for a potential client. Image via Wikileaks.
We come back to Miran International, who, whilst requesting a Non Disclosure Agreement (NDA) have listed their clients: Pakistan's Intelligence Bureau (IB) and Inter-Services Intelligence (ISI). “You can compare them to MI5 and MI6” Mr. Ali Ahmed offers helpfully. According to the Miran representative, “they're the only 2 agencies in Pakistan allowed to use voice interception and location products like A5-1 gsm interception systems.” (sic) *. “ISI and IB are the top agencies in Pakistan with no budget issues” he continues, “allowed to purchase without the tendering process.”
(*An example of what they could be referring to, for a point of reference, could be this: http://www.cellularintercept.com/ecom-prodshow/gsm_intercept.html)
Miran International and Hacking Team continue to discuss potential cooperation until early 2015, when internal emails between members of Hacking Team appear to look upon Miran International, and its sister company Vision Metric with some concern, and there is no update after February 26th of this year, when David Vincenzetti appears to remark that it is “una perdita di tempo” - a waste of time.
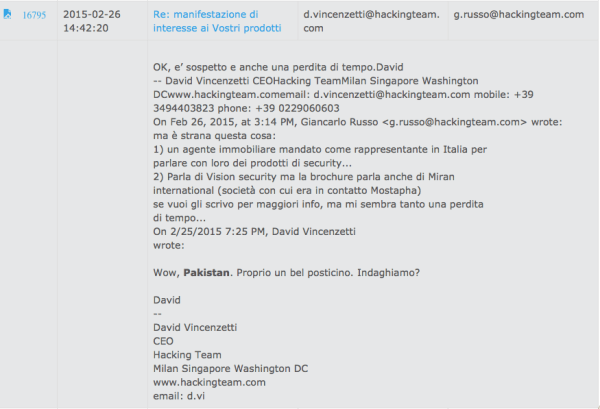
Hacking Team's CEO appears to have become fed up with this potential deal, calling it "a waste of time." Image via Wikileaks.
The communications between Hacking Team and Miran International may have been fruitless from the former's perspective, but a perusal of the communications between the two unearths other details. We learn, for instance, Gamma Group's representative in Pakistan was “very active in Islamabad with ISI” (sic) (though unsuccessful), and that Gamma Group's Sales Director, Edgar Bucheli, was in touch with senior ISI officials.
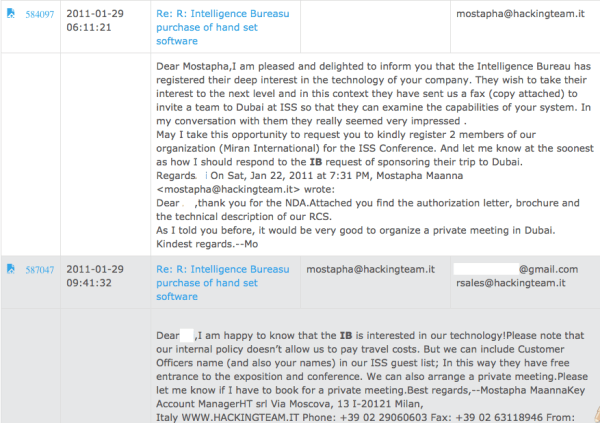
Here the representative passes on the information that the Intelligence Bureau (IB) is interested. Image via Wikileaks.
As for DSS, communications between them and Hacking Team continue until early 2014, and then stop, apparently due to a lack of success on the part of this company as well.
This does not stop Hacking Team from being approached by Pakistani companies, such as United International Technologies (UIT), which “has been in the Pakistan market for 35 years and is the Pakistan company representative for global defense and aerospace companies such as BAE Systems, Rockwell Collins, QinetiQ, Chemring Group and Poongsan among others.” UIT contacts Hacking Team via email on February 27th 2015, and until the 5th of March discuss NDAs and the “end users” or clients of UIT, “Pakistan Army Military Intelligence and/or ISI.” UIT informs them that they will be at the 2015 ISS conference in Dubai, from the 16th to the 18th of March. As of the 5th of March, UIT is “at a very preliminary stage.” Nothing else follows.
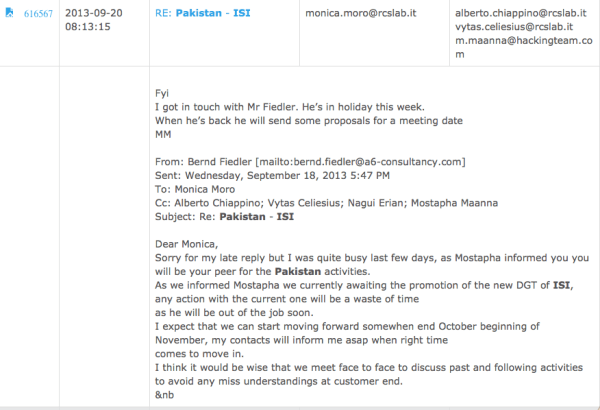
Hacking Team and its international partners discussing a new ISI head, as any work with the "current one is a waste of time.
What is noticeable about communications between Hacking Team and the representatives of potential client is the plainly laid out request for software that provides the customer with the ability to infiltrate and monitor communication traffic. What is conspicuous by their absence are any concerns raised about human rights or other ethical considerations.
The private companies mentioned in this post are just a few of the many that vie for contracts from the armed forces, the police forces and intelligence agencies of Pakistan, to offer the latest in software packages that ostensibly help protect the citizens of Pakistan. The reality is that the tools that are purchased on behalf of the forces and agencies mentioned are being chosen specifically because they are advertised as being able to bypass security measures that allow users privacy and a sense of safety, with next to nothing in terms of official restraint or public oversight.
To purchase and utilise such measures without clear lawful authority violates the rights of Pakistani citizens, as laid out in the International Covenant on Civil and Political Rights, to which Pakistan became a signatory in 2010. The representative from Miran International wrote in his email that ISI and IB have “no budget issues”. On the contrary, the money which pays for the supposed free rein of these agencies comes from the taxes paid by Pakistani citizens. With no public oversight, the taxes collected from citizens are being used to finance the purchase – or research the purchase of – equipment that violates their rights.
Privacy International's report, Tipping the scales: Security & surveillance in Pakistan, can be downloaded here.
Written by Adnan Chaudhri